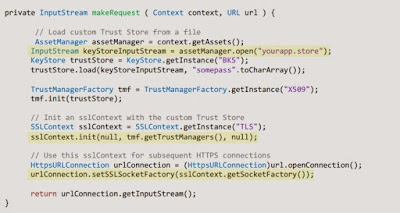
Code Obfuscation
When it comes to security of an application, Source code piracy is one of the major concerns. If your source code is available to hackers, it means you are totally screwed. Hackers can then easily bypass your applied security controls, re-build application with malicious code snippets and also misuse the business logic used in the application. Obfuscation is the process of renaming the meta-data in an Assembly so that it is no longer useful to a hacker, but remains usable to the machine for executing the intended operations. It does not modify the actual instructions or mask them from observation by a hacker. Reverse engineering of your proprietary applications by unfair competition or malicious hackers may result in highly undesirable exposure of your algorithms and ideas, proprietary data formats, licensing and security mechanisms, and, most importantly, your customers' data. Getting into more details about Code Obfuscation as given below. Name Obfuscation: Na